WordPress owes its widespread adoption to its flexibility, extensive plugin and theme ecosystem, and user-friendly interface, making it an ideal choice for individuals, small businesses, and large enterprises alike. From blogs to e-commerce stores, WordPress supports a wide range of functionalities, all without requiring extensive technical expertise. However, this very versatility comes with a cost: the platform’s popularity means it is under constant scrutiny from cybercriminals seeking to exploit vulnerabilities. With thousands of plugins and themes, often developed by independent contributors with varying levels of security expertise, the ecosystem can inadvertently introduce weaknesses into a website’s defenses.
Moreover, WordPress’s open-source nature, while a strength for innovation and community-driven improvements, also provides hackers with access to its underlying code, enabling them to identify and exploit potential flaws. Combined with human factors like weak password management or the neglect of updates, WordPress websites can become attractive targets for attacks ranging from data breaches to malware injections. For website owners, understanding these risks and implementing proactive security measures—such as regular updates, strong passwords, and reliable security plugins—is essential to safeguard their sites against evolving threats. Prioritizing security not only protects sensitive data but also preserves user trust and ensures a positive reputation online.
Request a Free WordPress Vulnerability Scan today!
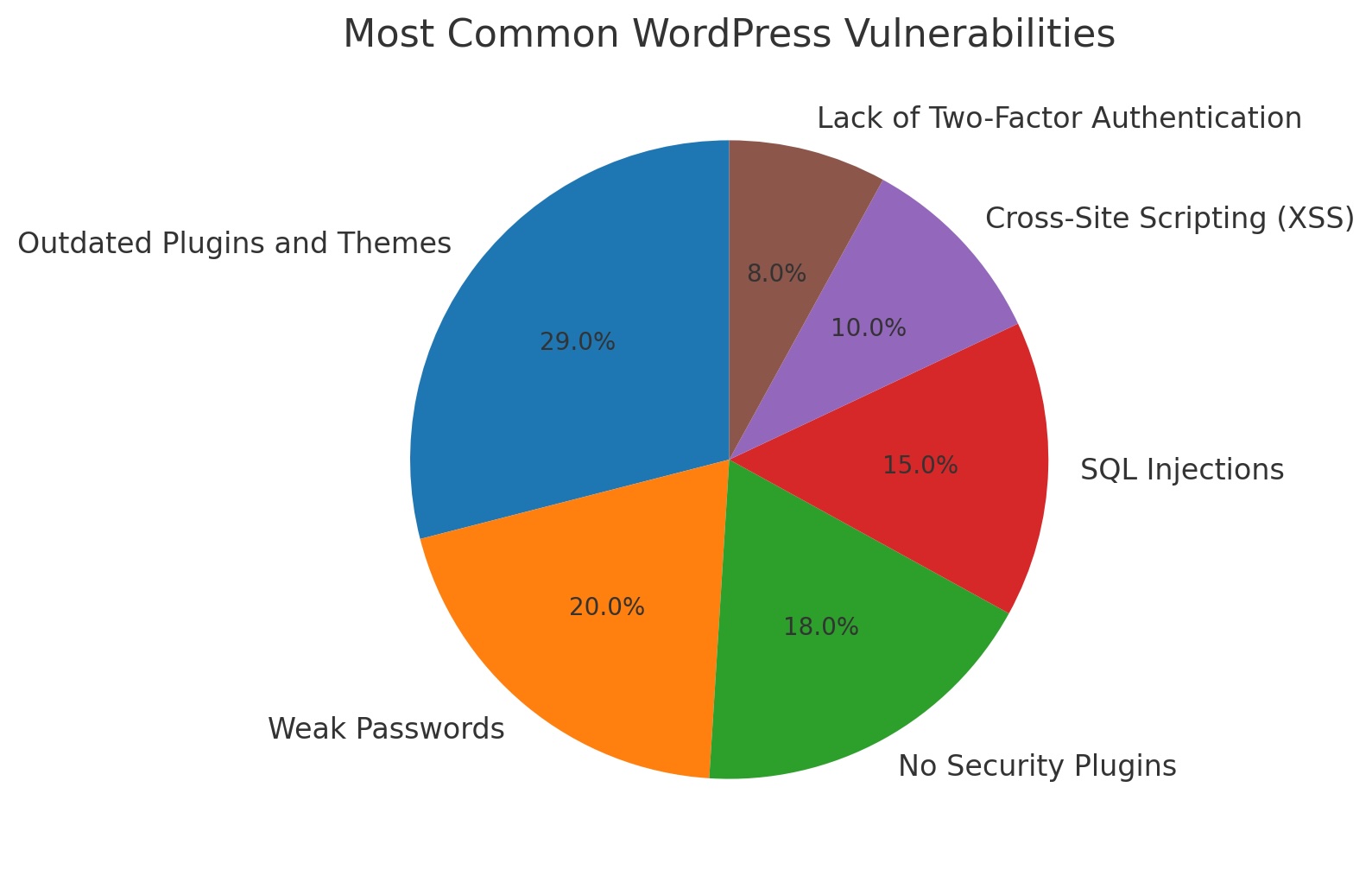
1. Outdated Core, Plugins, and Themes
Vulnerability
Outdated WordPress installations, plugins, and themes are the most common vulnerabilities. Developers regularly release updates to patch security holes, but sites that fail to apply these updates remain vulnerable.
Example: TimThumb Vulnerability
The TimThumb library, once a popular image resizing tool in WordPress themes, was exploited widely in 2011 due to a Remote File Inclusion (RFI) vulnerability. Hackers could upload malicious scripts to compromised websites.
Mitigation
- Enable automatic updates for WordPress core, themes, and plugins.
- Regularly check for updates and ensure compatibility before applying them.
- Remove unused plugins and themes.
2. Weak Passwords
Vulnerability
Using weak passwords, such as “password123” or “admin,” makes brute force attacks simple for hackers. Attackers use automated tools to guess login credentials.
Example: Brute Force Attacks on Admin Accounts
Hackers target WordPress admin panels with common username-password combinations. If successful, they gain full control of the site.
Mitigation
- Use strong, unique passwords for all accounts.
- Implement two-factor authentication (2FA).
- Use plugins like Wordfence or Login LockDown to limit login attempts.
3. SQL Injection
Vulnerability
SQL Injection (SQLi) occurs when attackers insert malicious SQL statements into input fields, compromising the database.
Example: WP Statistics Plugin Vulnerability (2022)
A vulnerability in the WP Statistics plugin allowed attackers to inject SQL commands, exposing sensitive data.
Mitigation
- Use plugins from reputable developers.
- Employ a Web Application Firewall (WAF) to block SQL injection attempts.
- Regularly scan for vulnerabilities using tools like Sucuri.
4. Cross-Site Scripting (XSS)
Vulnerability
In XSS attacks, hackers inject malicious scripts into web pages, which execute when visitors interact with the page.
Example: GDPR Cookie Consent Plugin Vulnerability (2020)
A stored XSS vulnerability in this plugin allowed attackers to inject scripts into the admin panel, compromising the website.
Mitigation
- Validate and sanitize all user inputs.
- Use security plugins like WP Cerber or iThemes Security.
- Keep all components of WordPress updated.
5. File Upload Vulnerabilities
Vulnerability
Improper file upload handling allows attackers to upload malicious files, such as PHP shells, that can be executed on the server.
Example: Contact Form Plugins
Several contact form plugins have been exploited in the past due to insecure file upload mechanisms, allowing hackers to upload and execute malicious files.
Mitigation
- Restrict allowed file types for uploads.
- Use plugins with secure file upload implementations.
- Scan uploaded files for malicious content using a security plugin.
6. Privilege Escalation
Vulnerability
Privilege escalation vulnerabilities occur when attackers gain unauthorized access to higher-level privileges, such as admin rights.
Example: User Role Editor Plugin (2020)
A vulnerability allowed non-admin users to modify their roles and gain admin privileges.
Mitigation
- Limit the number of admin users.
- Use role management plugins to define strict permissions.
- Regularly audit user roles and privileges.
7. Unsecured APIs and Endpoints
Vulnerability
APIs and endpoints can be exploited if they lack proper authentication and validation mechanisms.
Example: REST API Vulnerability (2017)
A vulnerability in the WordPress REST API allowed attackers to modify posts and inject malicious content.
Mitigation
- Disable unused APIs.
- Restrict API access using authentication tokens.
- Monitor API activity for suspicious behavior.
8. Directory Traversal
Vulnerability
Directory traversal vulnerabilities allow attackers to access sensitive files on the server, such as wp-config.php.
Example: Gallery Plugin Vulnerability
A flaw in some gallery plugins allowed attackers to traverse directories and retrieve sensitive files.
Mitigation
- Restrict access to sensitive files using
.htaccessrules. - Use secure file permissions (e.g., 644 for files and 755 for directories).
- Regularly scan for vulnerabilities.
How We Can Help
While WordPress vulnerabilities are common, addressing them is entirely manageable with the right approach and tools. Regular updates to the WordPress core, themes, and plugins are among the simplest yet most effective measures to close security gaps. Strong credentials, including complex passwords and multi-factor authentication (MFA), significantly reduce the risk of brute force attacks. Robust security plugins, such as Wordfence, Sucuri, or iThemes Security, offer additional layers of protection by monitoring for malware, blocking suspicious activity, and safeguarding against threats like SQL injections and XSS attacks. However, staying ahead of potential risks also requires vigilance, including regular security audits to identify weak points and remaining informed about emerging threats in the WordPress ecosystem.
This is where Majaid Web Solutions can provide invaluable expertise. Specializing in WordPress and WooCommerce development, Majaid Web Solutions offers tailored security solutions designed to protect your website from evolving threats. Their team conducts comprehensive security audits to uncover vulnerabilities, implements advanced security protocols, and ensures that your WordPress environment remains up to date. With deep expertise in WordPress architecture, they can optimize your site’s defenses, from configuring secure hosting environments to deploying firewalls and intrusion detection systems. Additionally, Majaid Web Solutions provides ongoing support, monitoring your site for potential issues and offering rapid response to any incidents. By partnering with Majaid Web Solutions, you gain peace of mind knowing your WordPress site is protected by professionals who prioritize its security as much as its functionality.
Need help with WordPress security?
Request a Free WordPress Vulnerability Scan today!